Summary
Cryptography is the study of secure communications techniques that allow only the sender and intended recipient of a message to view its contents. with added benefit of being able to prove the correctness of the message and the identity of sender. Very valuable indeed.
The term is derived from the Greek word kryptos, which means hidden.
It is closely associated to encryption, which is It is closely associated to encryption, which is the act of scrambling ordinary text into what’s known as ciphertext and then back again upon arrival
Advantageous properties (how it is different than encryption)
- confidentiality messages are impossible to read for everyone except the intended recipients.
- integrity impossible to modify content without detection.
- non-repudiation authenticity of the message can be validated.
Symmetric key cryptography
A shared secret is exchanged privately and the messages are decrypted(understood) on by the bearers of the secret. Efficient encryption and decryption: less computation resources needed.
Public key cryptography
Limitation of symmetric key cryptography is exchange of private key, public key cryptography only the public is shared and private key never leaves the owner.
Not efficient: computationally expensive.
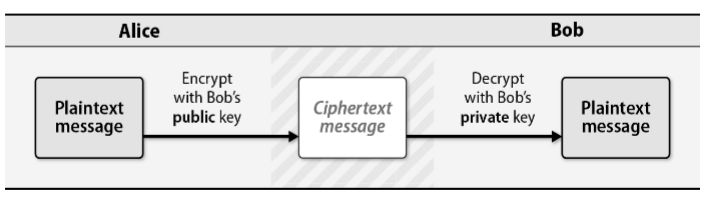
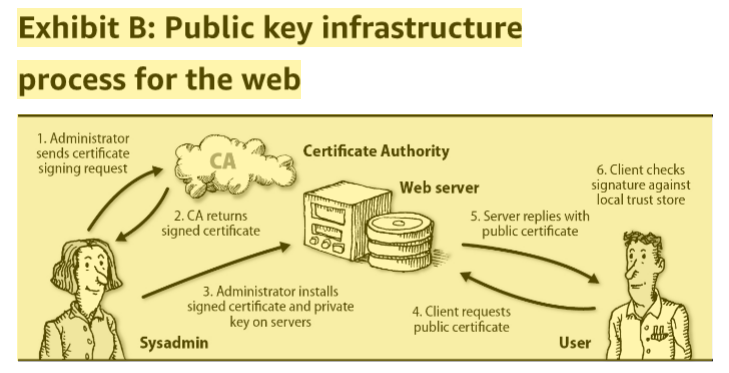
Validating the authenticity of public keys at Internet scale is a formidable challenge. The Public Key Infrastructure, used to implement TLS on the web, address this problem by trusting a third party known as Certificate Authority(CA) to vouch for public keys. CA issues SSL Certificate certificate that the clients(e.g. browser) can trust using trust chain.
Hash functions
Math functions that generate the ciphertext
Desirable properties:
- Entanglement every bit of the hash value depends on every bit of the input data. On average, changing on bit of input should cause 50% of the has bits to change.
- Pseduo-randomness hash should be indistinguishable from the random data.
- Nonreversibilty should be computationally infeasible to discover another input that generates the same value of hash.
Cryptographic hash algorithms
SHA-2(SHA-256) and SHA-3 are recommended and secure. SHA-1 has been comprosmised. MD5 is not as secure.