Related
The Problem:
| position | ease | box | interval | due |
|---|---|---|---|---|
| front | 2.5 | 0 | 0 | 2021-09-12T08:03:13Z |
- Man in the middle attack, hacker tricks client to believe that his/her machine is the actual server or sends email with link to initial a transaction on original site.
- CSRF client tricks server to believe that it is the intended client.
-
Assuming that the user is currently accessing “http://bank.com”, logged in
-
Also user has opened a malicious website, which is similar to the bank.com, that has below content
-
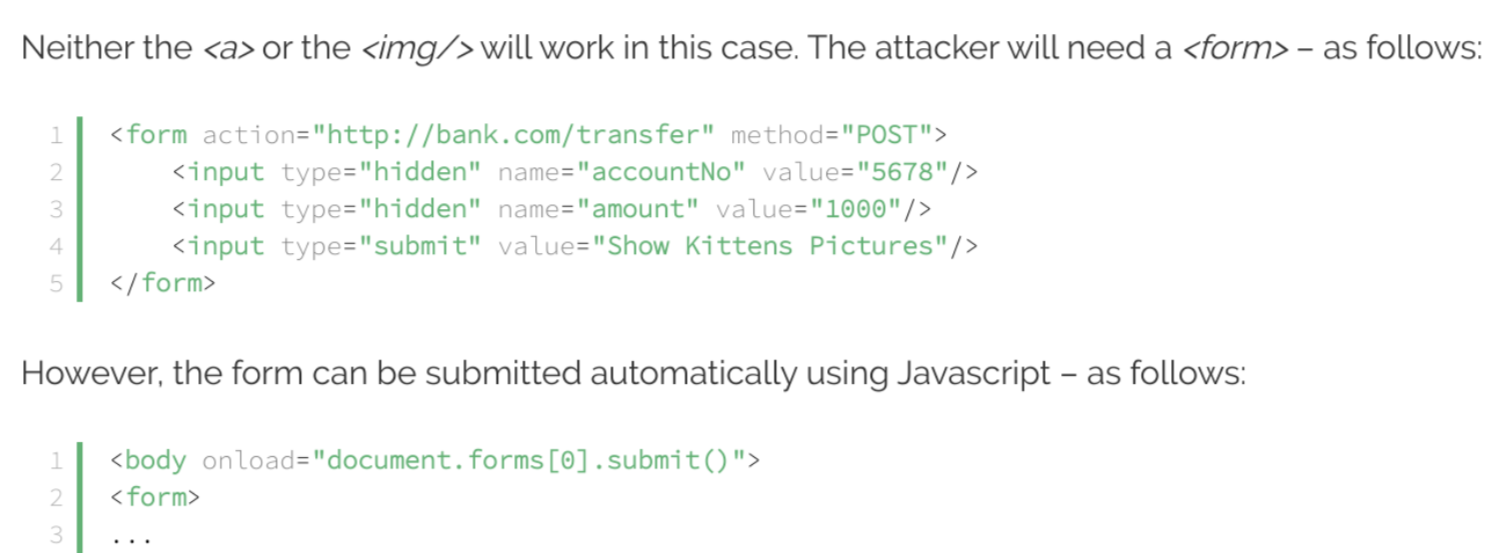
-
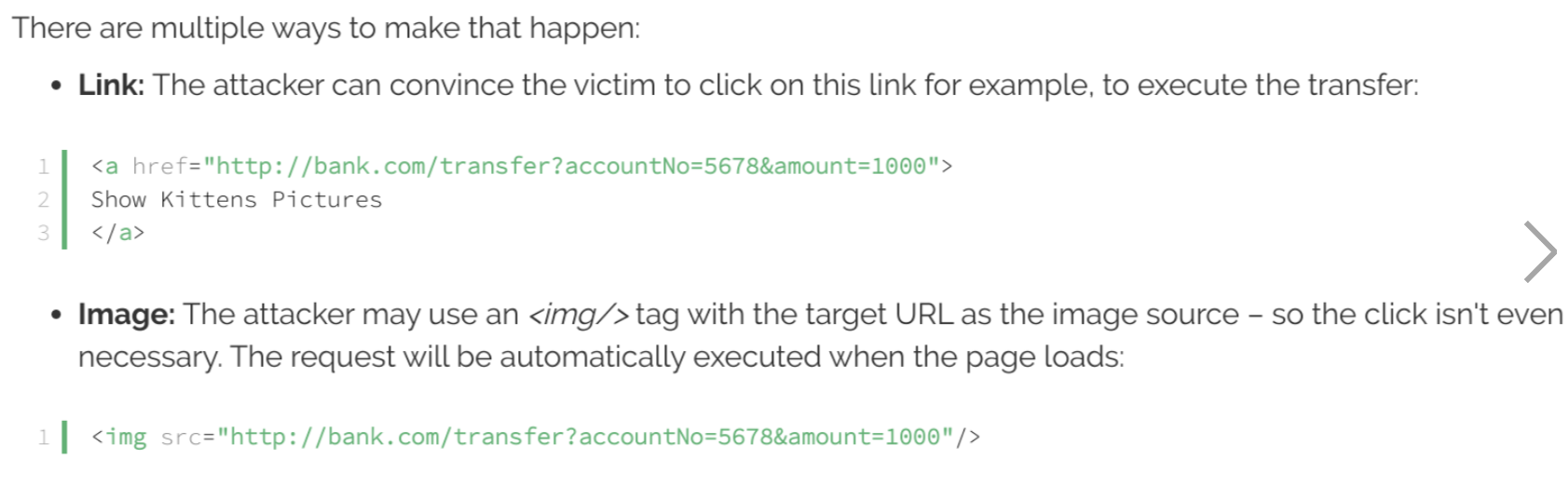
-
The solution:
- Make it mandatory for client to also send an additional token, which server validates, along with every post request
- Server sends this token to intended client as HTTP response
<form action="" method="post">
{% csrf_token %}
</form>
3. Although this token is present in the HTML sent to the intended client, the Malicious website cannot access it because of . Note: for more details check