What is SCIM?
ref Over the last few years, the world has been moving from on-premises to cloud-based environments. In this migration process, identity provisioning becomes a critical factor due to confidentiality concerns and the security of user data. The System for Cross-domain Identity Management (SCIM) specification is designed as an open standard for managing user identity in cloud-based applications and services easier, faster, and cheaper. This specification suite seeks to build upon experience with existing schemas and deployments, placing specific emphasis on the simplicity of development and integration while applying existing authentication, authorization, and privacy models.
According to the rfc7642 specification:
The system for Cross-Domain Identity Management (SCIM) is designed to manage user identity in cloud-based applictions and services in a standardized way to enable interoperability, security, and scalability.
What problem it solves?
Problem?
When new person joins org
- Multile manual accounts creation
- e.g., HR manager will have to create a new account into cloud based and local systems.
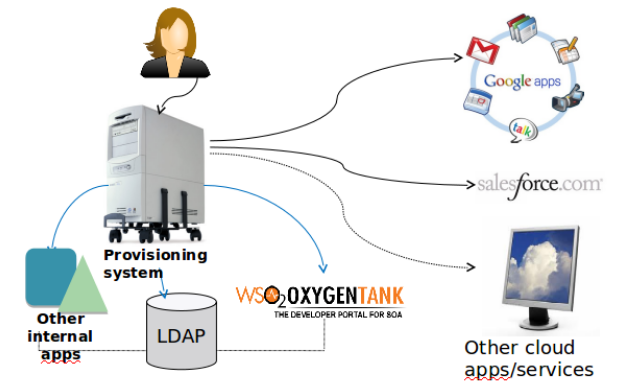
Solution?
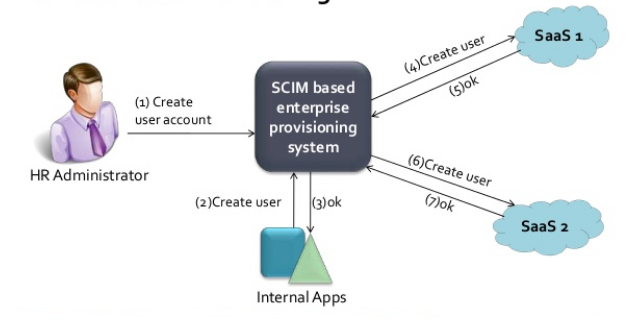
Connector’s problem
We use connectors at KFUPM
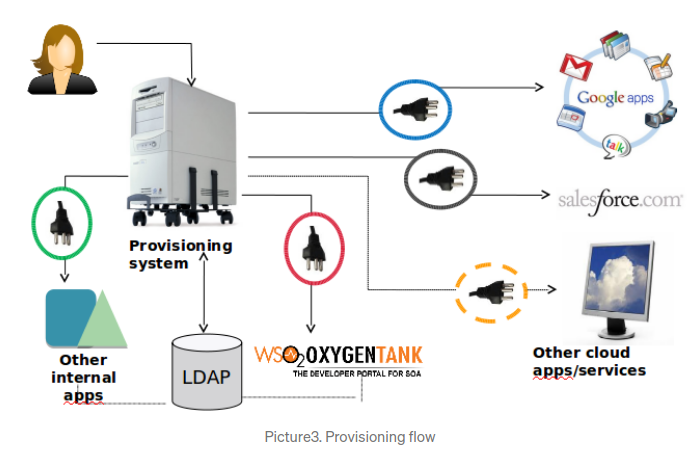
-
Issues
- Redundant integration efforts for ECS & CSP.(See picture4)
- Maintenance nightmare of multiple connectors.
- Complexity and cost.
- Independment user management in each system(KFUPM), connection is one way at KFUPM.
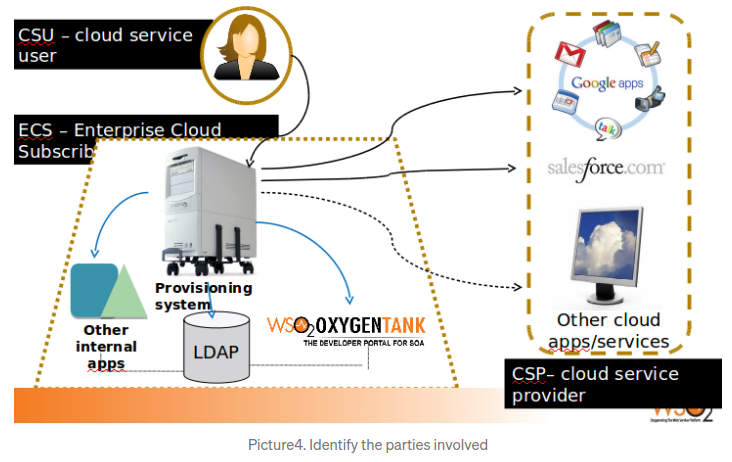 *
*
Solution
SCIM

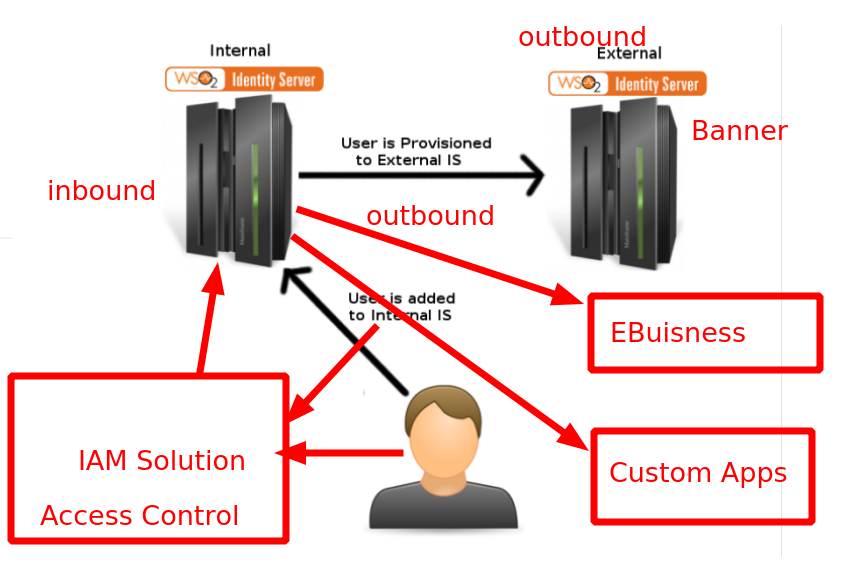
Banner Ellucian integration with SCIM
SCIM Usecases
Migration of the identities
The company ABC has stored identity information of its employees in a cloud service provider CSP_X and they want to move the identities into a cloud provider CSP_Y without changing the format of identity information.
SSO service
Bob has an account in an application hosted by a cloud service provider CSP_X. CSP_X has federated its user identities with a cloud service provider CSP_Z. When Bob accesses an application hosted in CSP_Z, it relies on Bob’s authentication by CSP_X.
Provisioning of user accounts for a Community of Interest
Organization ABC provides HR services to a Community of Interest (COI) COI_X. COI_X has offices all over the world and user information is collected through the regional offices. Organization ABC services provide means for provisioning and distributing the employee identity information across all COI_X offices enabling the employees to access applications running on private and public clouds.
Transfer of attributes to a relying party’s website
Bob has an account in a directory service ABC with one or more attributes. Bob then visits the website of the relying party XYZ and the website requires attributes of the user. Bob selects some attributes and authorizes the transfer of data via authorization protocols (e.g., OAuth, SAML), so selected attributes of the user are transferred from the user’s account in directory service ABC to the website of the relying party XYZ at the time of Bob’s first visit to that site.
Change notification
Bob has an account in a directory service ABC with one or more attributes. Bob then visits the website of the relying party XYZ and the website requires attributes of the user. The website queries directory service ABC for attributes associated with Bob and related resources. Then Bob may decide to change his name or to terminate the relationship with directory service ABC and directory service ABC will notify these changes to the relying party XYZ.
Groups and Roles in SCIM
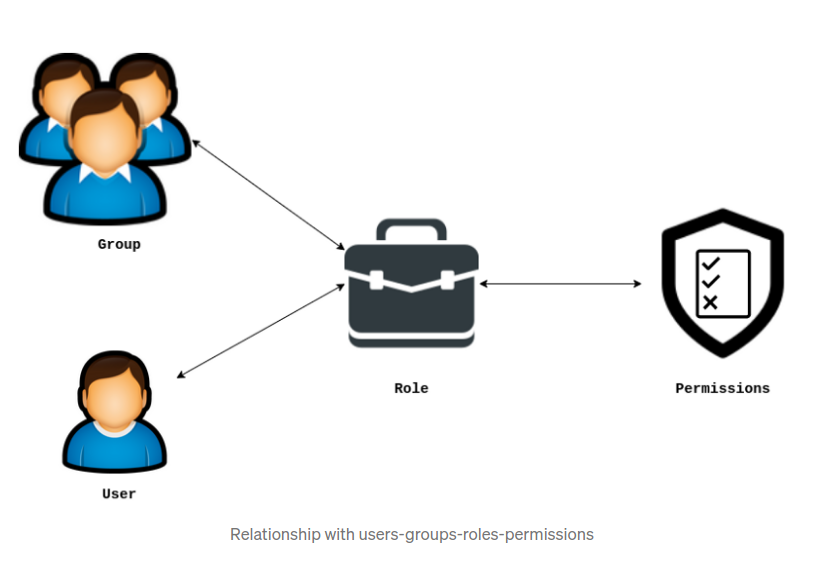
Definitions
Even though we supported both Groups and Roles together those two terms have different meanings when comes to computer science security.