Summary
The Secure Shell Protocol (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network.[1] Its most notable applications are remote login and command-line execution. ref
Essentials
-
ssh the client
-
sshd the server
-
ssh-keygen for generating public/private key pairs
-
ssh-add and ssh-agent tools for managing authentication keys. ssh-agent caches the decrypted private key. You load your private keys into the agent, and ssh then automatically offers those keys when it connects to new servers, simplifying the process of connecting.
-
sftp-server the server process for file transfer over SFTP
-
sftp and scp file transfer client utilities
ssh-agent forwarding
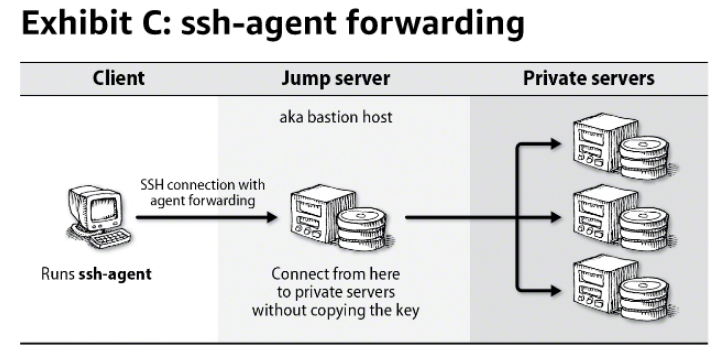 They cannot read your private keys directly, but they can use any that are available through the
agent forwarding.
They cannot read your private keys directly, but they can use any that are available through the
agent forwarding.
host aliases
Connection multiplexing
Improves performances over . When enabled, the first connection to a host creates a that can be reused. Subsequent connections share the but requires separate authentication.
Known_hosts
while connecting to server with ssh, the server sends back the public key for verification. If the server isn’t already known and trusted , ssh prompts the user to confirm the server by presenting a hash of the server’s public key called key fingerprint:
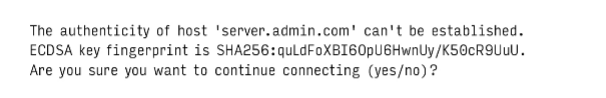
The intent is that the server administrator can communicate the host key to users in advance. Users can then compare the information they received from the administrator to the server’s proffered fingerprint when they first connect. If the two match, the host’s identity is proved.
~/.ssh/known_hosts
Commonly used commands
To run a command on remote server
ssh apps-3.test.kfupm.edu.sa "df ~"
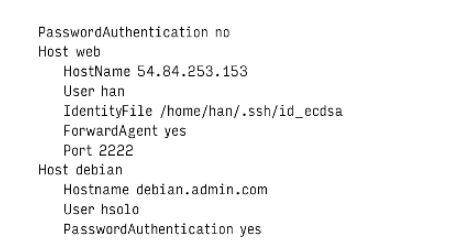
ssh_config
ssh reads configuration settings from the site-wide file “etc/ssh/ssh_config” and process additional
options and override on a per-user basis from /.ssh/config.
Public key authentication
Public key is given to the server administrator, who adds it to the server in the file “~/.ssh/authorized_keys”. You can login onto the remote server by running ssh with remote username and matching private key.
Port forwarding
To access not exposed port on server through ssh tunneling.
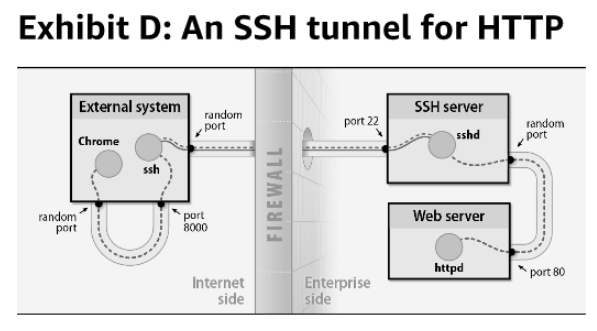
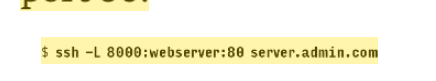
port 80 of the server will be accessible as 8000 on local machine, through SSH tunnel.
ssh-keyscan
# command to generate host has with public key for host key verfication
ssh-keyscan -H -t ed25519 courses-1.kfupm.edu.sa
# this will be added to /etc/ssh/ssh_known_hosts