How it works?
uses TLS protocol.
Random
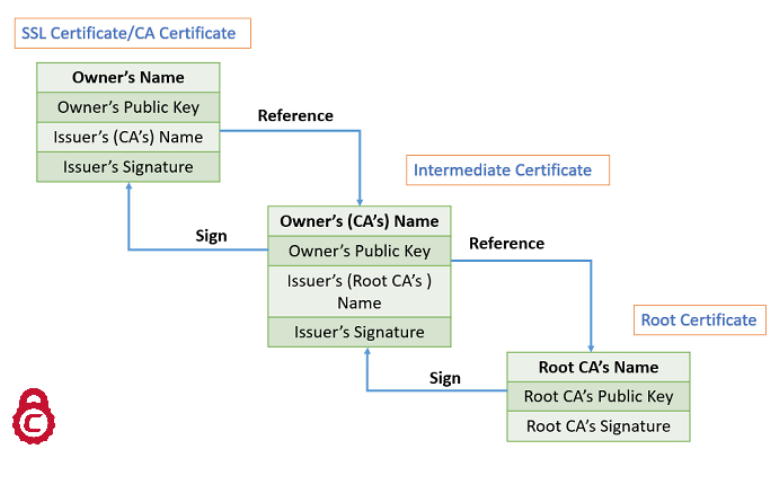
Signing is done with private key and data or information is encoded with public key.
Certificate chain or hierarchy and content fc
| position | ease | box | interval | due |
|---|---|---|---|---|
| front | 2.5 | 0 | 0 | 2021-09-29T16:49:52Z |
Certificate content
SSL certificates include:
- The domain name that the certificate was issued for
- Which person, organization, or device it was issued to
- Which certificate authority issued it
- The certificate authority’s digital signature
- Associated subdomains
- Issue date of the certificate
- Expiration date of the certificate
- The public key (the private key is kept secret)*
Chain
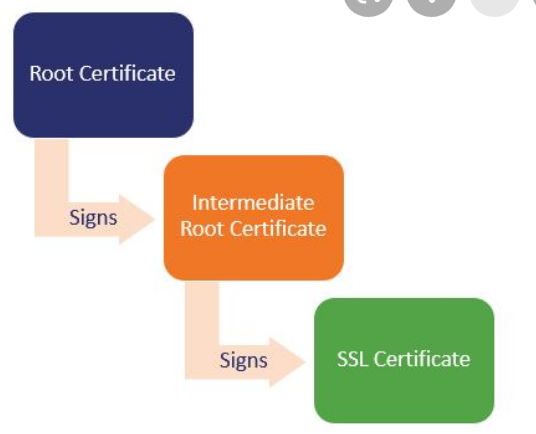
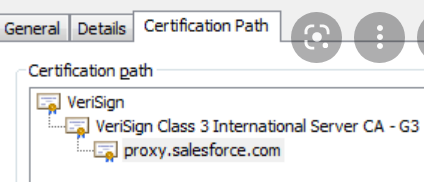
Certificate content and signature
Signing is done with private key
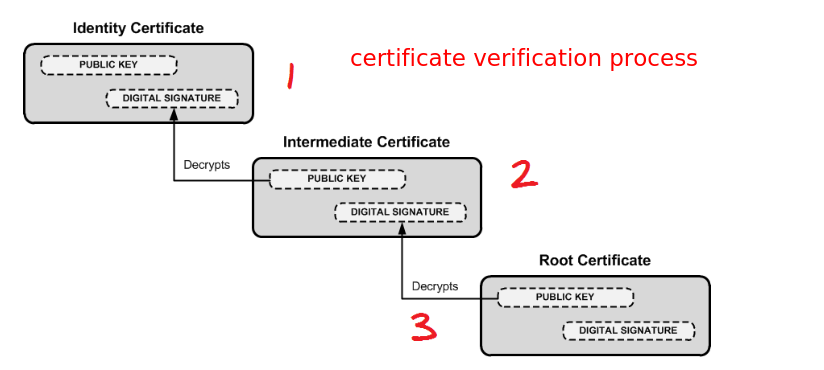
Verification chain
Purchasing
is good source to purchase cheap SSL ceritificates. I purchased ’s projects’s certificate from here.
Certificates will be emailed by on after purchase
sends certificate zip file that contains both bundle certificate(root + intermediate CA certificates) + leaf certificate.
Adding SSL certificate
To
<VirtualHost 192.168.0.1:443>
DocumentRoot /var/www/html2
ServerName www.yourdomain.com
SSLEngine on
SSLCertificateFile /path/to/your_domain_name.crt
SSLCertificateKeyFile /path/to/your_private.key
SSLCertificateChainFile /path/to/cabundle.crt # bundle.crt
</VirtualHost>
To
Create ssl_certificate
config details ssl_certificate For the client to recognize the certificate, the complete chain should be bundled in and `ssl_certificate` should point to the that bundle.
-
Lesson learned
In project, “ssl_certificate” was pointing to just root or intermediate CA, this was causing following issues
- The ssl certificate on “ksaflyer.com” domain was getting displayed as invalid.
- In the app of the project, the images were not getting rendered because of the SSL issue: Image component was throwing SSL, java, invalidpath? issue. Bundling the SSL certificate as describe in the example below worked
-
Bundling the SSL certificate
cat your_domain.crt your_domain.ca-bundle >> ssl-bundle.crtserver { listen 443; ssl on; #** ssl_certificate /etc/ssl/ssl-bundle.crt; #** ssl_certificate_key /etc/ssl/ssl-tutorials.key;#** server_name ssl-tutorials.com; access_log /var/log/nginx/nginx.vhost.access.log; error_log /var/log/nginx/nginx.vhost.error.log; location / { root /var/www/; index index.html; } }
Debugging SSL issues?
openssl s_client -connect ksaflyer.com:443 -showcerts
Start Time: 1632912777
Timeout : 7200 (sec)
Verify return code: 21 (unable to verify the first certificate)
Extended master secret: yes
Tools to verify SSL certificates
https://www.sslshopper.com/certificate-decoder.html
Glossary
CA Bundle
ref CA bundle is a file that contains root and intermediate certificates.
Certificate chain
The end-entity certificate along with a CA bundle constitutes the certificate chain.
Certificate Authority(CA)
ref A third party organization which is used to confirm the relationship between a party to the HTTPS transaction and that party’s public key. Certification authorities may be widely known and trusted institutions for internet based transactions. Though where HTTPS is used on a company’s internal networks, an internal department within the company may fulfill the role of a CA.
The certificates of major CAs such as GeoTrust and VerifSign are bundled with operating systems distribution.
CA authorities charges some amount to sign and verify your SSL Certificate getting issue.
Digital Signature
ref A digital signature (not to be confused with a digital certificate) is electronic. It can be used with any kind of message, whether it is encrypted or not, so that the receiver can be sure of the sender’s identity and that the message arrived intact.
A digital certificate is an electronic certificate file which contains a digital signature. SSL Certificates are a type of digital certificate. SSL certificates contain the digital signature of the Certificate Authority (CA) that issued it. CAs are companies authorized to create SSL certificates. Browsers can check an SSL certificate’s digital signature to verify that the certificate is real.
Additional benefits to the use of a digital signature are that it is easily transportable, cannot be easily repudiated, cannot be imitated by someone else, and can be automatically time-stamped.
Encryption
Symmetric
Encryption is the process of changing readable data (also referred to as “plaintext”) into a form that can be read only by the intended receiver. To decipher the message, the receiver of the encrypted data must have the proper decryption key. In traditional encryption schemes, the sender and the receiver use the same key to encrypt and decrypt data – this is a type of encryption known as symmetric encryption.
Asymmetric or Public-key encryption
SSL uses a more advanced form of encryption called Public-Key encryption. In Public-key systems, there are two keys: a public key, which anyone may use, and a corresponding private key, which is possessed only by the person who created it – which in this case is the webserver’s administrator. With this method, anyone may send a message encrypted with the owner’s public key, but only the owner has the private key necessary to decrypt it. This allows secure encryption over the Internet. Public-key encryption is a type of encryption called asymmetric encryption because different keys are used for encryption and decryption.
Root Certificate
An SSL certificate issued from Certificate Authority (CA). These certificates are distributed to millions of computers so that they can successfully use SSL certificates from those CAs. Devices such as desktops, laptops, smartphones, and printers contain Root Certificates.
SSL Key
The Private Key is sometimes referred to as the SSL Key. Your server must have a Private Key to function properly and you should always keep it secure and not share it with outside parties. With this key your secure communications can be decrypted. See Private Key for more
SSL Handshake
The SSL handshake is the term given to the process of the browser and web server setting up an SSL session. The SSL handshake involves the browser receiving the SSL certificate and then sending “challenge” data to the web server in order to cryptographically prove whether the web server holds the SSL key associated with the SSL certificate. If the cryptographic challenge is successful then the SSL handshake has completed and the web server will hold an SSL session with the web browser. During an SSL session the data transmitted between the web server and web browser will be encrypted. The SSL handshake takes only a fraction of a second to complete.