Provisioning
ref Provisioning means Create, maintain and delete user accounts and related identities in one or more systems or applications.
Inbound provisioning
Users coming from other applications - inbound. User is created in App1, if the IS want that user to be created in IS as well, then IS must be configured in inbound provisioning.
Using Resident indentity provider
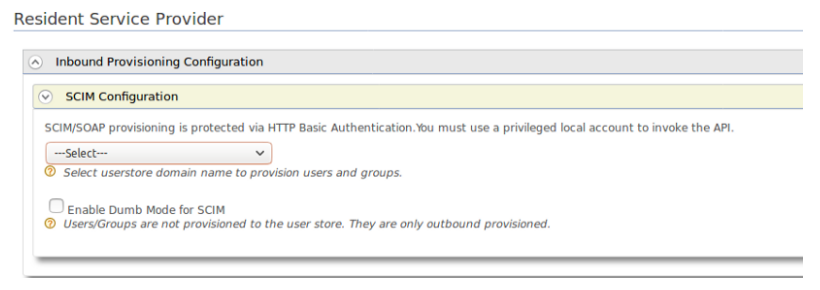 Here you have to select the user store in which you wanted to store the user.
You can send the scim request from your App1 to IS as follows
Here you have to select the user store in which you wanted to store the user.
You can send the scim request from your App1 to IS as follows
curl -v -k — user <user_name>:<password>— data “{“schemas”:[],”name”:{“familyName”:”kayal",”givenName”:”Nilasini"},”userName”:”nila",”password”:”nila2",”emails”:[{“primary”:true,”value”:”nilasini2@wso2.com”}]}” — header “Content-Type:application/json”
https://localhost:9443/wso2/scim/Users
Using service provider
When the application uses OAuth2, a service provider account should be created in the IS.
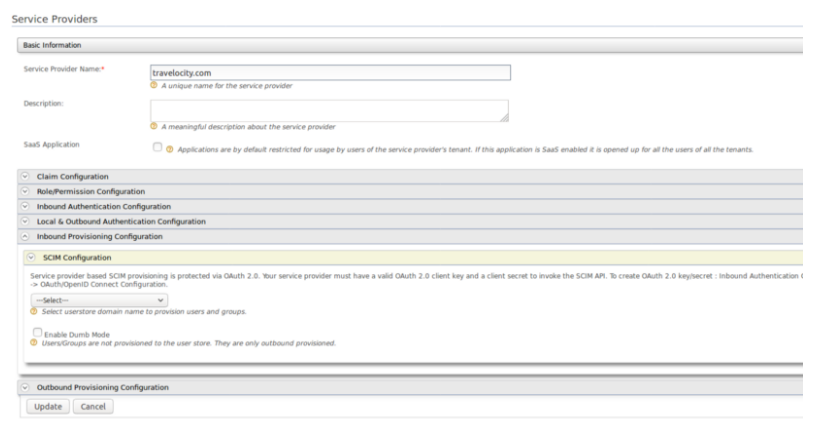
After that send the scim request (from App1 to IS) with the access token as follows.
curl -v -k — header “Authorization: Bearer <access_token>” — data ‘{“schemas”:[],”name”:{“familyName”:”fernando",”givenName”:”yohanna"},”userName”:”yohanna",”password”:”yohanna",”emails”:[{“primary”:true,”value”:”yohanna2@wso2.com”}]}’ — header “Content-Type:application/json”
https://localhost:9443/wso2/scim/Users
Outbound provisioning
Outbound provisioning means, when you create a user in identity server it must be created in the other application (name the application as APP2).
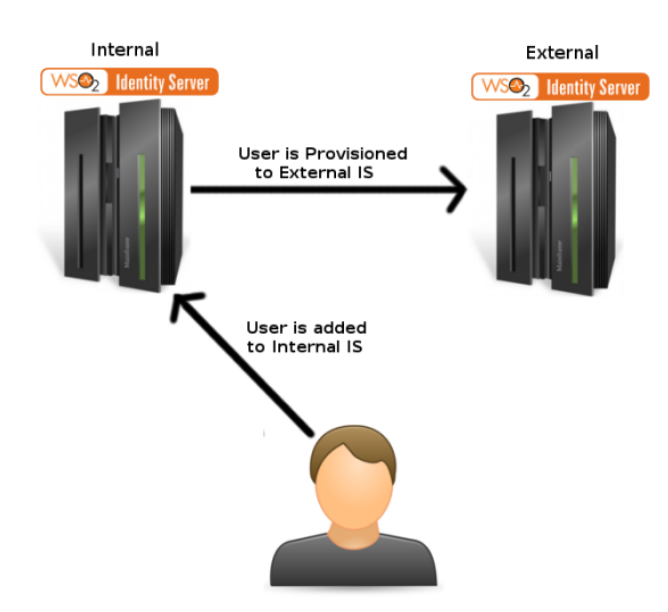 First I need to configure internal IS for outbound provisioning and then need to configure external
IS for inbound provisioning discussed above.TO do that first I need two IS instances. I am going to
use port off set to run two IS at the same time. To do that you need to execute the following
command when executing external IS so that it will run on port 9444 while internal IS will run in
the usual port 9443.
First I need to configure internal IS for outbound provisioning and then need to configure external
IS for inbound provisioning discussed above.TO do that first I need two IS instances. I am going to
use port off set to run two IS at the same time. To do that you need to execute the following
command when executing external IS so that it will run on port 9444 while internal IS will run in
the usual port 9443.
sh wso2server.sh -DportOffset=1
Configure internal IS for outbound provisioning
First thing you need to create an Identity provider (that identity provider is external IS) with following configuration.(You can add IP using “add” under the Identity provider in the left pane of WSO2).
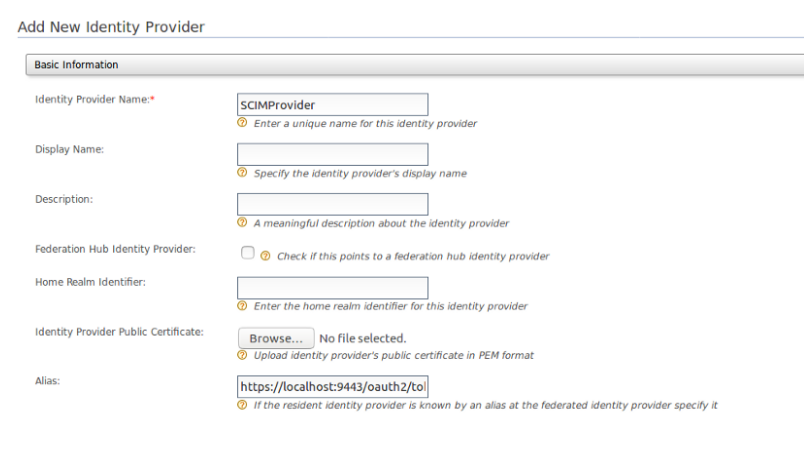
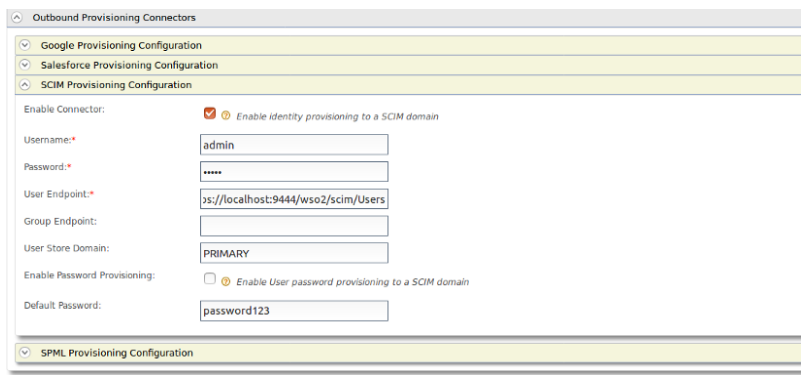 This outbound provision connector has the endpoint and authentication details of the external IS.
This outbound provision connector has the endpoint and authentication details of the external IS.
Configure external IS for inbound provisioning
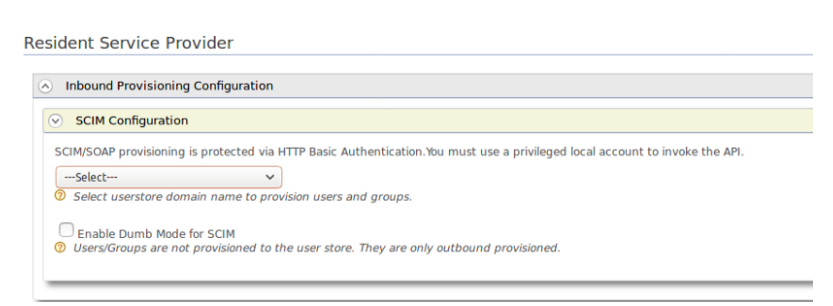
JIT provisioning
JIT provisioning which allows to create user accounts automatically for the sign-on users in the Identity Server.Just-in-time provisioning talks about how to provision users to the identity server — at the time of federated authentication.
SCIM
- Implemented as native feature from 5.6.0, earlier it was available as an extension, ref.
Configurations
Adding multiple callback URLs to the service provider
- Access the Management Console via https://localhost:9443/carbon/.
- Navigate to Service Providers > List and Edit the service provider that you created for the OAuth2 application.
- Edit the Callback URL field and enter a logout URL along with the callback URL that you defined when you created the service provider.
- regexp=(callback_url|logout_url)
You can specify multiple callback URLs using a regex pattern as follows: Example:
regexp=(http://localhost:8080/playground2/oauth2client|http://localhost:8080/playground2/logout)
Claim mapping when using multiple user stores
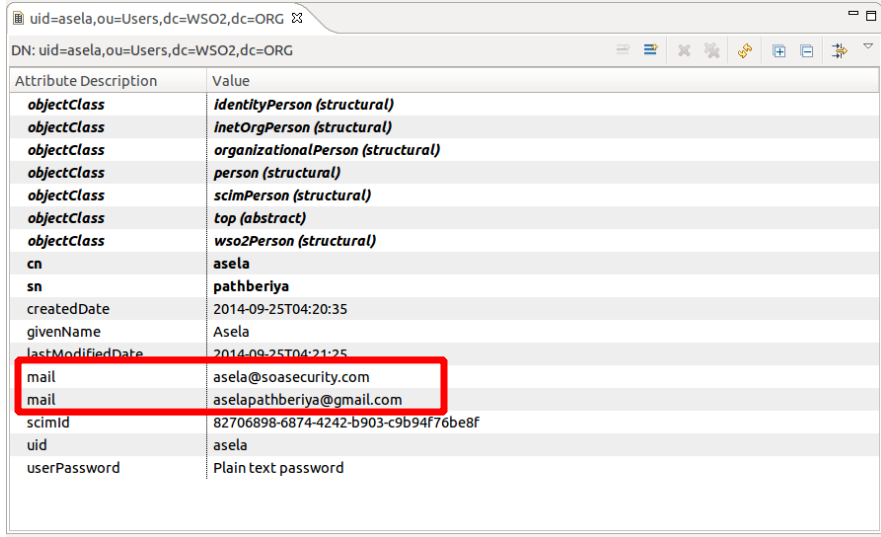 When mail is mapped as claim, it will appear as comma seperated values of mail in string format.
When mail is mapped as claim, it will appear as comma seperated values of mail in string format.
APIs
APIs to manage Service providers
Applications
API’s to import and export application, service provider’s, configurations, and to manage applications(SP configurations). These API’s will also get all the related configuration of the application. Roles and Permissions can also be managed.
Roles and permission management
- “updateApplication” endpoint with “PermissionsAndRoleConfig” with config.
Permissions required to invoke Admin services
Scopes
OpenID Scope
These are the scopes that bind to user attributes(WSO2 claims). You can use OIDC scopes to limit access user’s attributes. Managing openid scopes: list scopes asocciated and edit them, add or remove.
OAuth2 Scope
These are the scopes that bind to roles (DEFAULT) and permissions(PERMISSION). By default these scopes will be bind to roles, but if you want you can bind these to permissions as well. For now, in WSO2 Identity Server Permission binding is used in the internal purpose only
Inbound vs Outbound authentication?
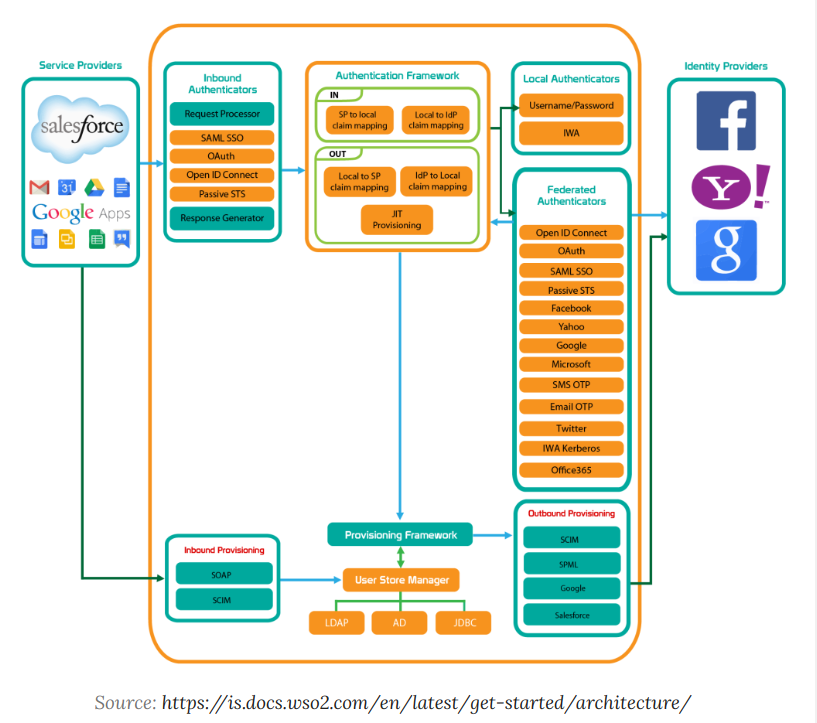 Inbound -> authenticate locally
Outbound -> use external IP to handle authentication.
Inbound -> authenticate locally
Outbound -> use external IP to handle authentication.
https://buddhimawijeweera.wordpress.com/2021/07/25/introduction-to-wso2-identity-server/ Good definitions of vocabulary here.